Top Open Source Alternatives To HashiCorp Vault
A curated list of open source alternatives to HashiCorp Vault
HashiCorp Vault is a powerful tool for securely managing and storing secrets, such as API keys, passwords, and other sensitive information. It provides a centralized location for managing access to these secrets and offers features like encryption, access control, and audit logging.
Key Features Include:
-
Identity-Based Security: Authenticates and authorizes access to secrets based on verified identities using various methods such as tokens, usernames, passwords, and multi-factor authentication.
-
Secrets Management: Handles various types of sensitive data including passwords, certificates, and API keys. Secrets are encrypted before storage to ensure protection both at rest and in transit.
-
Dynamic Secrets: Generates unique credentials on demand that can be automatically revoked or expired when no longer needed, reducing the risks associated with static credentials.
-
Key Management: Provides secure storage and handling of cryptographic keys, supporting symmetric, asymmetric, and HMAC keys without exposing them to clients.
-
Integration with Identity Providers: Seamlessly integrates with multiple identity providers (IdPs) like Active Directory and LDAP for centralized user authentication and authorization.
-
Audit Logging: Records detailed logs of all access activities for compliance and security monitoring.
-
Encryption as a Service: Offers encryption capabilities for data in transit and at rest, ensuring sensitive information remains protected.
-
Support for Multiple Environments: Manages secrets across various environments including cloud providers, on-premises data centers, and hybrid setups.
-
Revocation Capabilities: Allows users to revoke secrets before their lease expiry, enabling granular control over access management.
-
Disaster Recovery Features: Provides options for disaster recovery replication to ensure high availability and resilience.
HashiCorp Vault is essential for organizations looking to enhance their security posture by effectively managing sensitive credentials in a dynamic infrastructure.

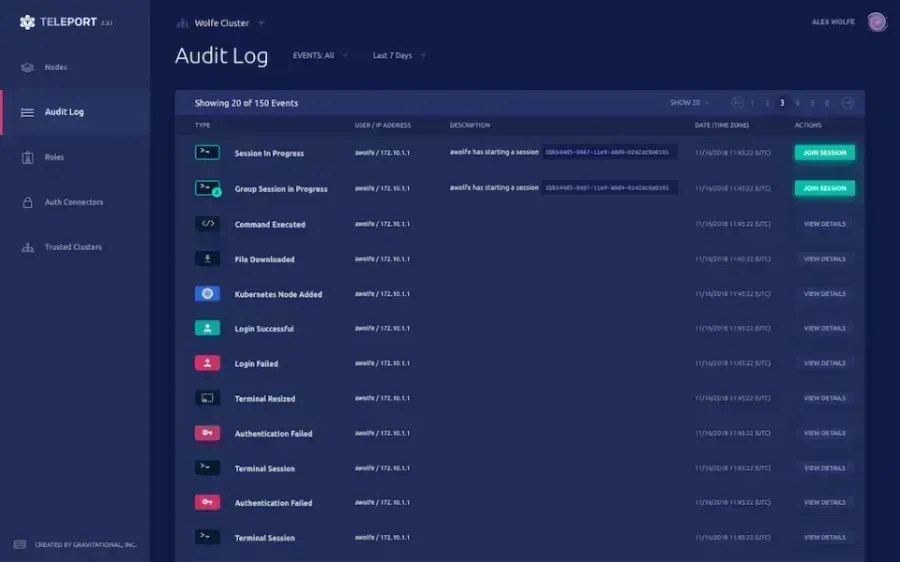
Teleport
Teleport is a secure infrastructure access platform that provides on-demand, least-privileged access to infrastructure using zero trust principles.

Hoop
Hoop is an open-source platform that provides secure access management, automated data protection, and streamlined workflows for development teams.